Description
Sow Ching Shiong, an independent vulnerability researcher has discovered a Password Reset vulnerability in www.facebook.com, which can be exploited by an attacker to bypass certain security restrictions.
In normal circumstances, an authenticated Facebook user is required to enter his/her current password on the change password page to prevent an unauthorized person from changing the password without the user's knowledge.
However, an attacker can change/reset a user's password without knowing the user's current password by accessing this URL directly: https://www.facebook.com/hacked.
After that, the page will be redirected to https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked
Now, the attacker can click "Continue" to change/reset the user's password.
Proof of concept
Step 1: Logon to Facebook and access this URL directly: https://www.facebook.com/hacked. The page will be redirected to https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked

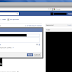
Step 2: Click on "Continue" to proceed

Step 3: Enter "New Password" and "Confirm Password" to change/reset the password.

Conclusion
This vulnerability has been confirmed and patched by Facebook Security Team. I would like to thank them for their quick response to my report.
Facebook White Hat
https://www.facebook.com/whitehat
Sow Ching Shiong, an independent vulnerability researcher has discovered a Password Reset vulnerability in www.facebook.com, which can be exploited by an attacker to bypass certain security restrictions.
In normal circumstances, an authenticated Facebook user is required to enter his/her current password on the change password page to prevent an unauthorized person from changing the password without the user's knowledge.
However, an attacker can change/reset a user's password without knowing the user's current password by accessing this URL directly: https://www.facebook.com/hacked.
After that, the page will be redirected to https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked
Now, the attacker can click "Continue" to change/reset the user's password.
Proof of concept
Step 1: Logon to Facebook and access this URL directly: https://www.facebook.com/hacked. The page will be redirected to https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked

Step 2: Click on "Continue" to proceed

Step 3: Enter "New Password" and "Confirm Password" to change/reset the password.

Conclusion
This vulnerability has been confirmed and patched by Facebook Security Team. I would like to thank them for their quick response to my report.
Facebook White Hat
https://www.facebook.com/whitehat






.png)


.png)

.png)
.png)



.png)

